Researchers from the Kaspersky Endpoint security firm have identified Zero-day exploit from Google’s Chrome browser and Microsoft windows zero-day exploits that have targeted multiple attacks on several enterprises. Now the vulnerabilities have been patched in Microsoft’s recent Tuesday batch which was released by them on June 8th, 2021. This zero-day attack is called as PuzzleMaker.
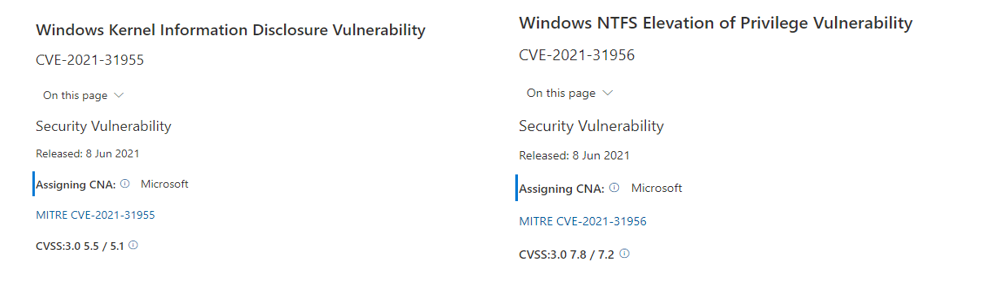
Kaspersky was able to find and analyse an elevation of Privilege (EoP) from the windows which exploited 2 vulnerabilities in the Windows OS kernel level. And these vulnerabilities were reported to Microsoft on April 20, 2021, and were assigned the CVE-2021-31955 to information disclosure vulnerability and CVE-2021-31956 to the elevation of Privilege, both the reported vulnerabilities were patched on Tuesday, June 8th, 2021.
Technical analysis of PuzzleMaker attack
As per the research, the attackers used 2 vulnerabilities from windows 10 to execute the malware execution to escape the “Sandbox” and also gained system access privileges.
Once they proceeded with the upload of malware module analysis, the team found that the malware exploits found additional malware modules such as,
- Stager
- Dropper
- Service
- Remote shell.
Where the stager module was successful in notifying the exploitation of the malware, also it downloads and executes the more complex module called Dropper from the remote servers. In stager module can deliver to the victims along with configuration details which define the CnC, URL (hxxps://p{removed}/metrika_upload/index.php), session ID, and Keys to decrypt the next stage of malware.
Next in the Dropper module is used to install the 2 executables that pretended to be the legitimate Microsoft Windows OS files. And the one file (%SYSTEM%\WmiPrvMon.exe) is registered as a service that helps to launch the second executable from windows. The other file (%SYSTEM%\wmimon.dll) is registered as a functionality of a remote code shell execution of the attacks payloads.
Here the remote Shell was a hardcoded with URL of the command and control server inside (media-seoengine[.]com). Communications between the victim and attacker are encrypted and authorized by the C&C server and client. And this remote shell can download and upload files, creation of processes, hibernate and finally delete itself from the victim’s system.
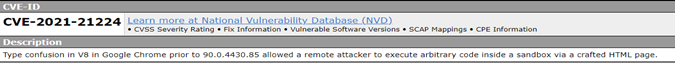
Finally, researchers found that PuzzleMaker used the Google Chrome browser to attack and after the investigation, it was concluded that attackers completely relied on the Vulnerability CVE-2021-21224 of Google Chrome.
And Kaspersky detects the malware and exploits as below,
- PDM:Exploit.Win32.Generic
- PDM:Trojan.Win32.Generic
- UDS:DangerousObject.Multi.Generic.
Indicators of Compromise (IoC) for PuzzleMaker attacks.
Domain: media-seoengine[.]com.
Files 1: %SYSTEM%\WmiPrvMon.exe.
MD5 09A5055DB44FC1C9E3ADD608EFFF038C
SHA-1 BFFA4462901B74DBFBFFAA3A3DB27DAA61211412
SHA-256 982F7C4700C75B81833D5D59AD29147C392B20C760FE36B200B541A0F841C8A9.
File 2: %SYSTEM%\wmimon.dll
MD5 D6B850C950379D5EE0F254F7164833E8
SHA-1 E63ED3B56A5F9A1EA5C92D3D2444196EA13BE94B
SHA-256 8A17279BA26C8FBE6966EA3300FDEFB1ADAE1B3ED68F76A7FC81413BD8C1A5F6.
