Recently malware analyst Karsten Hahn states that he has detected and analysed the file signed from Microsoft which is a rootkit called “Netfilter”. Netfilter is claimed to be official drivers from Microsoft as per the signature but the driver callout is redirecting the traffic to a Chinese IP address. Let’s see how this rootkit was detected in detail.
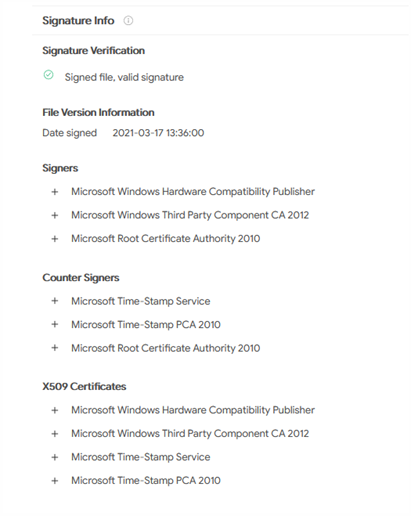
As per the Malware Analyst, they have received an alert notification because of driver detection, Netfilter signed from Microsoft. After receiving the alert analyst has forwarded the same to the Microsoft Threat investigation team for analysis, find out the rooting malware files had a signature from Microsoft which seems to have been compromised and the signing process is unknown.
Technical Analysis of Netfilter
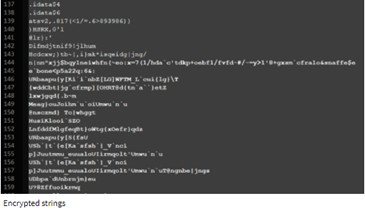
Initially, the strings that were observed during the first detection of the rootkit seems to be normal, but after decoding the files using python script it was malicious strings are present with suspicious IP address belongs to Chinese,
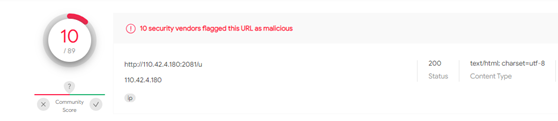
Upon checking the IOC in Virus total, it was detected that a few of the dropper files called Netfilter with signature dated back to March 2021.
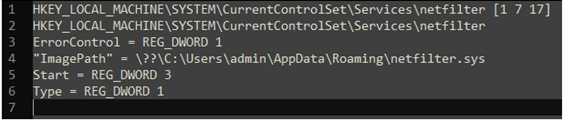
Dropper and Installation of the file was found to be into the dropper places in the drivers in “%APPDATA%\netfilter.sys” and then creates temp files in “%TEMP%\c.xalm” and issues the command to register the regini.exe x.calm to register the driver in the system as below,
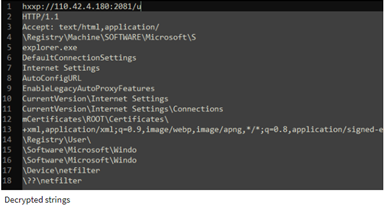
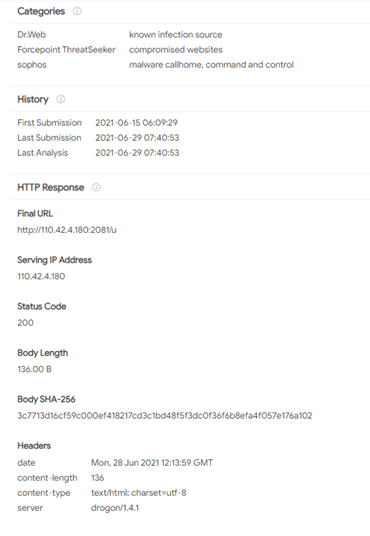
And after the URL “hxxp://110.42.4.180:2081/u” is decoded it registers the driver strings to the rootkit server and redirected to destination IP address 45.248(.)10.244. And the Netfilter drivers connect to the Command and Control server and server replies as,
Once the decoding and connecting with the server the rootkit certificate is provided via hxxp://110.42.4.180:2081/c and write copies to registry path: \Registry\Machine\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\ and the latest decoded reversed traffic was observed and provided to Pastebin by Johann Aydinbas in his Twitter account.
Indicators of Compromise (IoC) for Netfilter rootkit
Here, we can find the IOCs for the rootkit malware, and take necessary actions before there is a breach,
Hash Values
- 04e88b7717aadc6b56dfa006b9414fc2c899c398d7e003627770e07fed52edfd
- 4a229ab274e364df92cc46ecbc9faab32f7b0955dab982658313f2faf9410863
- 63d61549030fcf46ff1dc138122580b4364f0fe99e6b068bc6a3d6903656aff0
- 659e0d1b2405cadfa560fe648cbf6866720dd40bb6f4081d3dce2dffe20595d9
- 6c856c3c315c0f213684045da3203692c07c3da5df755155fd8b128fb447c437
- 8249e9c0ac0840a36d9a5b9ff3e217198a2f533159acd4bf3d9b0132cc079870
- 9804787b31e0025dd2ae9344ca1beae2e701cdf8fd77a60f424295dc9280dc89
- a3e8ea5e593176f9e66c17f6a200fa665c7ef409c97f49aadf5a55ad6b0be97e
- a5c873085f36f69f29bb8895eb199d42ce86b16da62c56680917149b97e6dac4
- b16c3ed44cd04b033621ada7f9ab89d830949b3c9dc26999d862ddbeb7cc5a86
- bbc58fd69ce5fed6691dd8d2084e9b728add808ffd5ea8b42ac284b686f77d9a
- bff9b75ae2eea49a765f79d9c67c997edb6c67a2cc720c6187dd2f67980acab7
- cb8e536680732b474a5c26970ace2087667622caa3dd82c1c56731a7c5a1c8ce
- d0a03a8905c4f695843bc4e9f2dd062b8fd7b0b00103236b5187ff3730750540
- d64f906376f21677d0585e93dae8b36248f94be7091b01fd1d4381916a326afe
- e0afb8b937a5907fbe55a1d1cc7574e9304007ef33fa80ff3896e997a1beaf37
- f83c357106a7d1d055b5cb75c8414aa3219354deb16ae9ee7efe8ee4c8c670ca
- 3c7713d16cf59c000ef418217cd3c1bd48f5f3dc0f36f6b8efa4f057e176a102
MD5 hash values
- 8a66ccf9261a0cc08a6ad085d6dd4055
- fd969b03b439284ff7a31c39cd336f25
- 0bd3b9f55a2d3a13f506d9d8b970e0de
- 83720e64aa1388d55324a22536bd39cd
- 5bf9f601188a4b11a8baf9b2abbd18fa
- 0e2d4679f68796e9dd0d663137cb9e12
- 145e3c224e4ecaf26d4638efb9d622a7
- 491a38f52692a88f5e97a1107c06a9f5
- 8bf00ef4dd6bb308c76849901b03ccbd
- 31d3f0ae33c72beff48c9459b132d24d
- 530f12f8058199964d0b41f1856185ec
- aa043913e02f124a4e7171fa40dfc9a2
- 400c1c6312f99e4640077994bbfaedde
- da6b25206a29c8ac9a8cbb4be5d3875c
- 1c3db7002523e1acd621c90701c694ae
- cb34374f1b5fb771076872c6b14b7501
- a57e4e3a3fa46bbdbc9d803283af3479
Few Sample hashes,
Netfilter driver – 63d61549030fcf46ff1dc138122580b4364f0fe99e6b068bc6a3d6903656aff0.
Netfilter dropper – d64f906376f21677d0585e93dae8b36248f94be7091b01fd1d4381916a326afe.
Netfilter driver, older version signed in March – 115034373fc0ec8f75fb075b7a7011b603259ecc0aca271445e559b5404a1406.
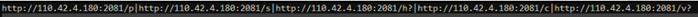
URL for block,
- hxxp://110.42.4.180:2081/p (Proxy settings).
- hxxp://110.42.4.180:2081/s (Redirection IPs)
- hxxp://110.42.4.180:2081/h? (Ping with CPU-ID)
- hxxp://110.42.4.180:2081/c (Root certificate)
- hxxp://110.42.4.180:2081/v? (Self-update)
- 45.248.10(.)244 – Redirected traffic to Chinese telecom.
