CAPTCHAs are challenges to prove the that users are humans, not a robot. But the cyber attackers are using these CAPTCHAs to their advantage to hide the malware or phishing campaigns in Google’s reCAPTCHA’s.
According to the researchers from Palo Alto, hiding the malware content behind CAPTCHAs prevents the security crawlers from detecting malicious contents and ads and gives a legitimate view to login phishing sites. And according to the researcher from the past long month has observed around 7500+ unique malicious URLs over 4000+ pay-level domains employing the Obfuscation method. So as an average of 529 new CAPTCHA-protected malicious URLs has been observed per day.
How to detect CAPTCHA-protected malicious sites?
Here, we can see the malicious campaigns across the domains and URLs.
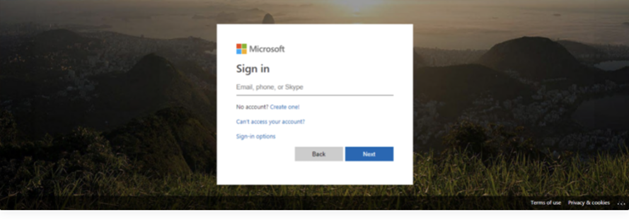
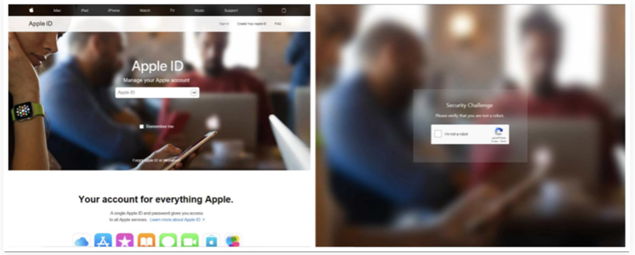
Microsoft and Apple Phishing ID credentials
Researchers have been monitoring long-running phishing campaigns for Apple since July 2020, the URL “hxxp://utem[.]com/[.]YSou8XI”. it’s been pushing phishing sites and targeting MS outlook, Apple, and other login pages.
For example,
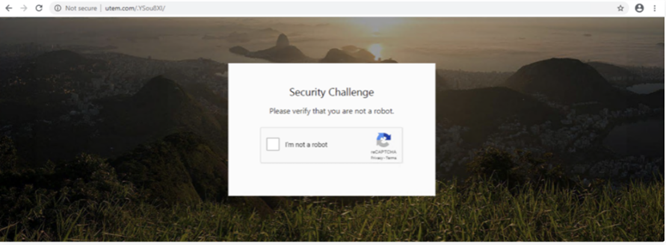
Once after resolving the CAPTCHAs, the page is redirected to classic phishing sites as below,
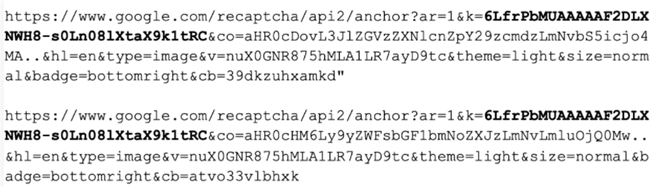
Here, however the threat researchers were able to identify the reCAPTCHA API key used in the URL parameters,
According to PALO Alto research team, Mass phishing and greyware campaigns have become more revealing for evasion techniques to escape the detections by security crawlers.
CAPTCHA IDs Signatures
We could see top 10 CAPTCHA identifiers which was by attackers to launch their malicious campaigns, here are the few lists of IDs to keep in watchlist, these unique lists of IDs launched more malicious sites by the cybercriminals.
CAPTCHA ID to Monitor
- 6LcEthAUAAAAANLeILVZiZpPDbVwyoQuQ7c3qlsy
- 6LcJK64UAAAAAKwjDYyWpakQ_5aFAb34tK-EkiDA.
- 6Le-dsYUAAAAABJa32oIuo9LEPsur7OcBz-a9kyL
- 6LfKnxEUAAAAAO1iXBX9FqL0w-68XqXGl3UPBF5p
- 6Lc8-cQUAAAAAF60sMK0PjhPOA6ciyzy6cfnGcl0
- 6LeihuEUAAAAAEgMRhYQKQCxnJvsqIZnRghJAPcH
- 6LezpHMUAAAAALunasQAvKdhRwFC1oqRE0OZW8f4
- 6LdkVo0aAAAAAN5yxjGbJPH39rF–s6ZVsl_LxzE
- 6LdVFrgUAAAAAEMNq1ljl8HZSQ2sA8Hu6a8umPQr
- 6LfrPbMUAAAAAF2DLXNWH8-s0Ln08lXtaX9k1tRC
Conclusion:
CAPTCHAs ID are example of a malicious indicator and attackers use it to detect phishing, malware and greyware pages. Fortunately, malicious actors use infrastructure, services or tools across their malicious websites to leverage these indicators against such attacks.
Indicators of Compromise
List of 7000+ IOCs can be found here in GitHub.
