In the recent reports, it is stated that major countries like Russia, India & China have adopted a new technique called “RTF Template Injection” which has made a major change and their attacks are harder to detect and mitigate. And this technique has been adopted by financially motivated threat actors as well.
RTF template Injection
Threat researchers from vendor Proofpoint have observed the Implementation of the RTF technique using Phishing attachments by APT hacker groups. The technique uses Microsoft office features which use the templates stored locally or downloaded from a remote server for the attack technique known as “Remote Template Injections”.
The attackers use malicious office files like DOC, XLS, PPT to send to the victims through email Spear-phishing campaign and once the user downloads the content the malicious code will load via template using Office app.
According to the threat researchers, the users must click the button which says “Enable Content” or “Enabling Editing” which is also known as a security warning and blocks the automatic template’s malicious code as per Microsoft, but it hasn’t been efficient at blocking the MS suite attacks in years as the per Proofpoint.
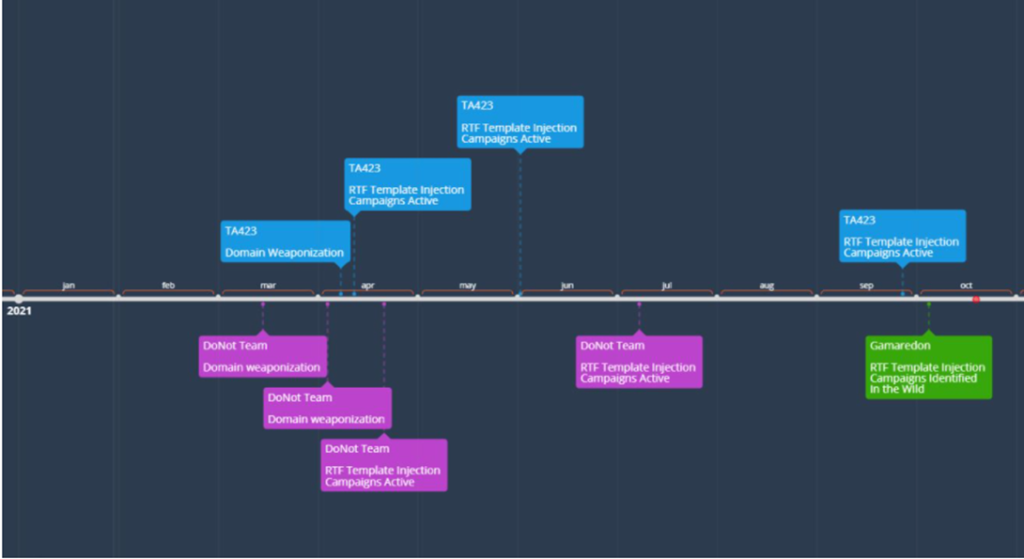
APT adopting RTF template Injection
As per the threat researchers, it is been used by three state-sponsored groups which are Gamaredon (Russia), TA423 (China), DoNoT (India). Initially, the technique was used by DoNot & TA423 using RTF documents with malicious code in the template early this year 2021.
Indicators of Compromise analysed during the research,
- 801402ffa0f0db6cc8fc74c68c4b707a625205f25bc2c379f6a8b8329231eb56
- 694d433a729b65993dae758e862077c2d82c92018e8e310e121e1fa051567dba
- 9525.rtf|a33ccc612a03de4f42a6f5ab5277470f6a7e8ee7abe52725b13704366e8da48b
- 9525.doc|8f4a91ecfb9190461459a2d05e5cb944da80ec30a2b1d69f9817ecb431a5ac8f
- edc84bbf13b8300540daf7cd203dc12eede6286a1ac5ce2175031fba3125d354
- Зразок тлг ІСД ІНТЕРНЕТ.docx|066b2b884b250a3bda4feb19aaa71616c19bf6387ed2767b633521647ada29f8
- Акт інсталяції.docx|b9aefe12015489b94e9e7d2cc19fd5e81a471da93a320477f1c8e362344f6bde
- hxxp://pretence77.glorious.nonima[.]ru/ELENAPC/principles/nearly.mp3
- hxxp://intense52.faithful.onihik[.]ru/elenapc/
- hxxp://intense52.faithful.onihik[.]ru/ELENAPC/bikes.conf
Conclusion:
Researchers believe that Office-based remote template documents have proven the effective method for attacking the targets along with phishing techniques in the initial delivery of the malware to the victims. And they also believe that by enhancing this new technique the victims are being targeted by the threat actors by using the RTF technique by expanding the attaching surface worldwide.
The RTF technique may be increased in the case of minimal effort needed to inject RTF attachments in the phishing campaigns before deploying them.
