On May 30th, 2021, Threat Intelligence company Cyble reported a new incident to the Bombay Stock Exchange (BSE), National Stock Exchange (NSE).
A research team from Cyble performed an initial analysis of the attack and found that the attacker’s intention was not to store the financial details of their customers. Also, found that the Blackcocaine Ransomware gang is responsible for the attack on Nucleus Software Company which is an Indian IT Firm in Banking and financial services sectors.
Based on further analysis, it was found that Nucleus Software is the first target for the BlackCocaine Ransomware attack, as the domain operated by attackers was registered on 28th May 2021, as per WHOIS record details.
Blackcocaine Ransomware Technical Analysis
As per Cyble Researchers, the ransomware payload file is a UPX- packed 64-bit windows executable file programmed in Go language and complied in MinGW tool.
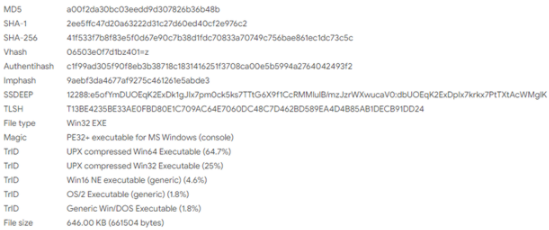
And Black cocaine Ransomware is capable of bypassing security measures of the target system as it has multiple anti-VM and anti-debugging techniques to protect from notifying the attack. Also on further analysis, it was found that Blackcocaine uses AES and RSA encryption techniques and ransomware operates on its own site: (hxxp://blackcocaine[.]top) similar to other ransomware gangs.

Here, the Ransomware decrypts the windows API during the runtime so the system can perform encryption on the victim files in the target machine. On successful completion of the file encryption of the victim files, Ransomware drops a note to the victims as “HOW_TO_RECOVER_FILES.BlackCocaine.txt”.
As per MITRE Attack TTP used in the ransomware attack was reported as – T1560 – Archive Collected Data, T1027 – Obfuscated Files or Information while targeting financial services, banking in countries like India, Singapore, Australia, Georgia.
Cyble team confirms that the black cocaine Ransomware follows the same model of server-side encryption to block the user document files from accessing and ask for the ransom to be paid. And the threat actors in the attack are known to use manual hacking techniques and open source tools. Also, the attackers look through the target network using lateral movement techniques before completing the encryption of the victim, then appends the extension with “.Blackcoaine” to the encrypted files.
Cyble team has still not yet confirmed about the initial infection vector of Blackcocaine infection which is about to be investigated. And below are some of the IoCs reported during the analysis.
Indicators of Compromise (IoCs):
FileHash-SHA256): “41f533f7b8f83e5f0d67e90c7b38d1fdc70833a70749c756bae861ec1dc73c5c”.
FileHash-SHA256): “6471a7f99df7a48e01bb7a7ebca3d638c5f6bf8f7feffd84f177cf969609819d”.
Domain: “blackcocaine[.]top/”.
URL: “hxxp://blackcocaine[.]top/”.
FileHash-MD5: a00f2da30bc03eedd9d307826b36b48b.
FileHash-SHA1: 2ee5ffc47d20a63222d31c27d60ed40cf2e976c2.
