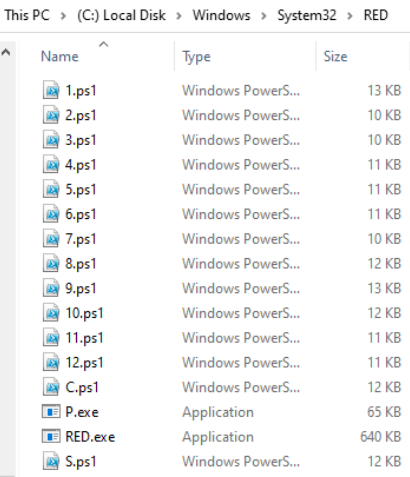
The new Ransomware Epsilon Red was discovered Sophos malware researchers. This Ransomware is written in the Go programming language which is called Epsilon Red. The malware mainly targets the unpatched Microsoft Exchange servers using the set of PowerShell Scripts.
According to the Sophos malware analysis, they confirm that every component of the attack completely relies on PowerShell scripts. Researchers also confirm the ransom note left by the attackers seems to be the same as REvil Ransomware attackers as per the TTP used in the breach.
Epsilon Red is a reference from the X-Men Marvel comics, a “super-soldier” based on a Russian origin with Mechanical tentacles and a bad attitude.
How this red ransomware works?
Security researchers from Sophos discovered the ransomware over the past week of investigating an attack from a Hospitality sector from a US Company. Epsilon red Ransomware relies on more than a dozen of scripts to reach the encryption of the data.
Initially, the attack was observed in the Enterprise Microsoft Exchange server as an entry point for the attackers which is unpatched vulnerabilities and this seems to be the root cause for this attack. Here, the attackers used WMI to install the exploits of hackers so they could reach the target network from the unpatched Exchange servers. In the Epsilon red ransomware, the threat actors launched a series of PowerShell scripts to encrypt the machines and final ransomware payload to deliver and execute it.
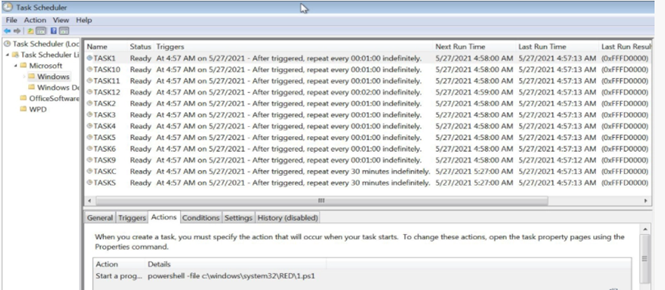
- Once after breaching the network, attackers use RDP protocol 3389 TCP Port and block the windows firewall for all incoming TCP traffic excluding the Remote Desktop Protocol and uses communication protocols such a Remote utilities (5650 TCP port) used by the commercial tools.
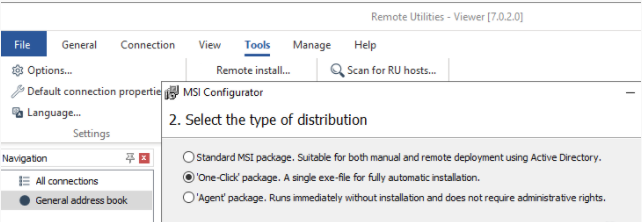
- Upon the successful breach, it was observed that attackers did install the Remote utilities and Tor browser on the target system as backup connectivity in case the initial access gets blocked. Commercial tools i.e. Remote Utilities used by attackers have multiple features which can be installed by anyone using their company mail IDs.
- After executing the Remote utilities in the target system, it found that attackers had generated the “One-Click installer” executables with the file name “rutserv.exe” which was installed in different systems in the network.
- File path: C:\Program Files (x86)\Microsoft Explorer\rutserv.exe,
- C:\Program Files (x86)\Windows Explorer\rutserv.exe,
- C:\Program Files (x86)\Windows.NET\rutserv.exe.
4. Before launching the ransomware, attackers involve tasks such as disabling the security tools installed in the system and backup tools and also killing the running processes that might interrupt the encryption of data on the hard drive.
- As mentioned this ransomware relies completely on dozens PowerShell Script, each PS Scripts plays a role in their tasks such as it executes and,
- deletes the volume shadow copies
- Disables the automatic repairs which tries to boot the windows.
- Delete the windows event logs.
- It also disables Windows defender by modifying the key value as: “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender” /f /v DisableAntiSpyware /t REG_DWORD /d.
- Finally file permissions on the system is modified as “Everyone” to machine groups to ensure as many files are encrypted.
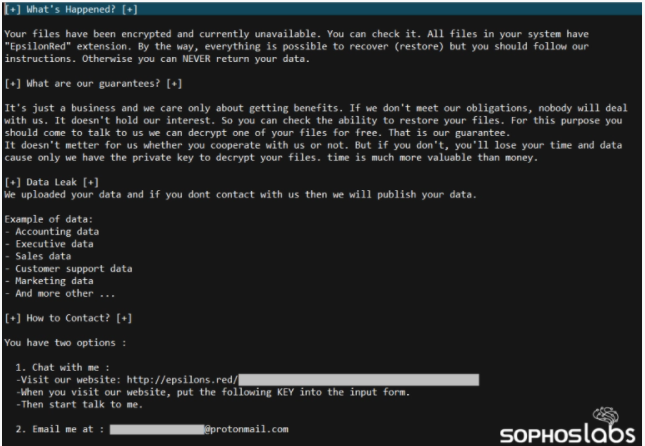
Ransomware hackers after all the processes followed by encryption displays the following Ransom notes to the victims which Incident responders suspect as similar to REvil Ransomware attackers due to the ransom notes left by the attacker seems almost the same which is part of Russian gang.
Recommendations
Sophos researchers suggests the victims of feature attacks to patch the internet-facing Exchange servers, Domain Controllers, or workstations.
Indicators Of Compromise for Epsilon Red Ransomware can be found here: Sophos Labs.
