Security researchers analyzed the Samsung smartphones and found multiple critical vulnerabilities that can be exploited by the hackers using Pre-installed applications.
As per the researchers, the vulnerabilities could exploit the phone, and attackers can access, edit the victims’ Calls, SMS/MMS, contacts, and install applications with the administrator privileges and can completely change the mobile system settings as per the attacker’s requirement.
Here, the researcher from Oversecured start-up published the patches that were issued by the manufacturer, there are seven vulnerabilities with affected applications as follows,
- CVE-2021-25356 – Installing third-party apps and granting those Device Admin permissions. Affected App: Managed Provisioning (com.android.managed provisioning)
- CVE-2021-25388 – Installation of arbitrary apps and device-wide theft of arbitrary files. Affected App: Knox Core (com.samsung.android.knox.containercore).
- CVE-2021-25390 – Intent redirection leads to gaining access to arbitrary content providers. Affected App: PhotoTable (com.android.dreams.phototable).
- CVE-2021-25391 – Gaining access to arbitrary* content providers. Affected App: Secure Folder (com.samsung.knox.securefolder).
- CVE-2021-25392 – Ability to steal notification policy configuration. Affected App: Samsung DeX System UI (com.samsung.desktopsystemui).
- CVE-2021-25393 – Gaining access to arbitrary* content providers leads to reading/write access to arbitrary files as a system user (UID 1000) Affected App: SecSettings (com.android.settings)
- CVE-2021-25397 – (Over-) writing arbitrary files as UID 1001 Affected App: TelephonyUI (com.samsung.android.app.telephonyui).
Vulnerability in Managed provisioning (CVE-2021-25356)
The Samsung devices are pre-installed with managed provisioning app which is used for corporate device customization. And originally this application is developed in Samsung to add features to interact with the ecosystem and Knox core.
Vulnerability in Knox core (CVE-2021-25388)
As per the researchers, the Knox core was scanned and discovered that it was installed on an SD card. And the functionality is activated through exported service: com.samsung.android.knox.containercore.provisioning.DualDARInitService:
An attacker could pass an arbitrary URI via dualdar-config-client-location parameter which will be copied to /sdcard/Android/data/com.samsung.android.knox.containercore/files/client_downloaded_knox_app.apk which is in a readable format. After which app installation process will be launched.
Proof of concept of arbitrary installation
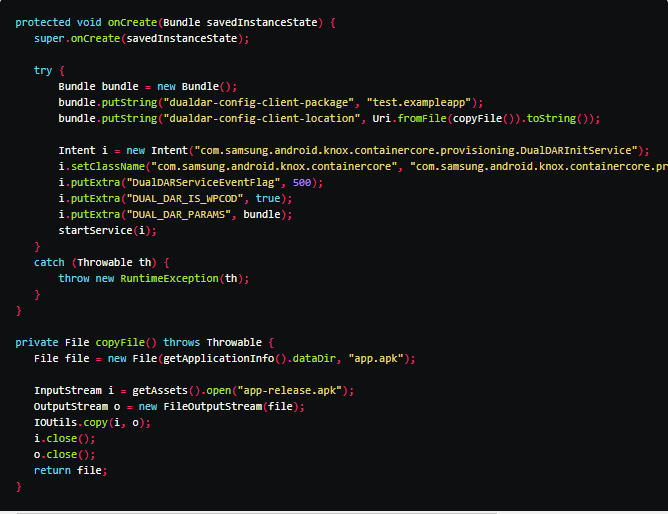
Vulnerability in PhotoTable (CVE-2021-25390)
In this vulnerability, the intent redirection was allowed access to content providers to be intercepted. And this is exploited to hijack the rights to access the SD card.
Vulnerability in Secure folder (CVE-2021-25391)
Its secure file storage app is pre-installed on Samsung devices. It is found to have a large set of rights for an attacker to exploit the vulnerability found in accessing: arbitrary* content providers.
Vulnerability in Samsung DeX system UI (CVE-2021-25392)
The attacker is allowed to steal data from the user notifications such as Gmail Inboxes, Samsung emails, chat descriptions of Telegram, WhatsApp, etc., Also, the attacker could activate the functionality to create a backup in the SD card, and hence the file will be deleted after the backup process is completed.
Vulnerability in SecSettings (CVE-2021-25393)
This is also a pre-installed settings app. The components of the vulnerability on reading and writing arbitrary files from UID 1000 (System) consists of
Gaining access to arbitrary* content providers
Exploiting the insecure Fileprovider in the com.sec.imsservice app.
Vulnerability in TelephoneUI (CVE-2021-25397)
As per the researcher, Oversecured Android scanner detected the receiver file: com.samsung.android.app.telephonyui.carrierui.photoring.model.PhotoringReceiver is exported and saves files from the URL specified in photoring_uri to the specified in down.File. And as a result with SMS/MMS messages were overwritten with attacker-controlled content.
Samsung phone after the attacks looked like this :
Conclusion:
Here is the list of vulnerabilities with the functionalities which was exploited and reported by the security researchers of oversecured. Samsung devices are recommended to apply the latest software updates that are released by the company to avoid data security risks from the Samsung smartphones.
