According to recent study researchers from 360 Fiberhome labs discovered the attack that mainly targeting Indian Military personnel using new Android spyware called PJobRAT malware.
The PJobRAT malware is spyware that is disguised as a genuine Indian dating application and instant messaging software. As per the researchers, the malware RAT family is first seen at the end of December 2019 and this mainly targets Indian Personnel with military-related backgrounds.
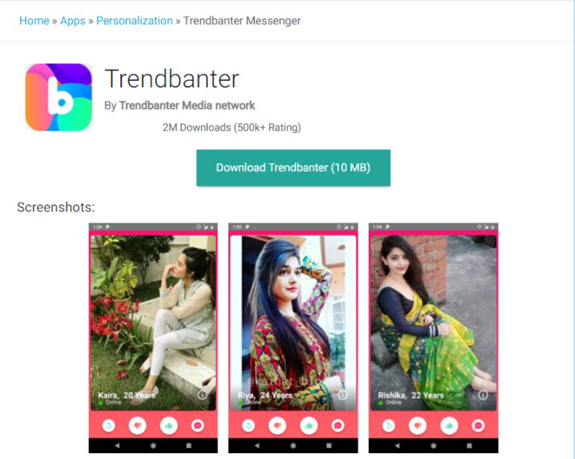
PJobRAT disguised as android application called Trendbanter which is the latest version for Indian dating and marriage applications. According to the markets Trendbanter is famous among thousands of NRI (Non-Resident Indians) who are not married and resides in the USA, Canada, Australia, Britain, and many parts of the world.

In addition to the above, it also said the PJobRAT spyware which is Trendbanter once installed in the mobile platforms it displays as a legitimate application such as Watsapp icon and some malware samples found to be displayed as Signal application icon which uses evading technique to hide within a mobile platform. And these settings which are displayed as the genuine application show that it is a spyware application installed.
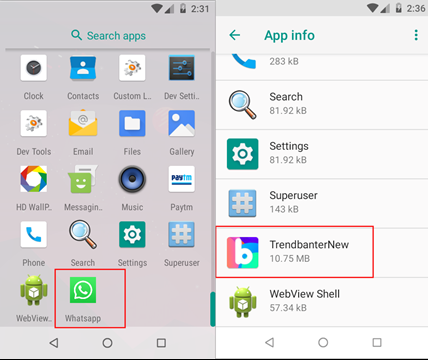
Technical Analysis of PJobRAT spyware
According to the associated malware samples, PJobRAT is the dangerous app that has permission to spy on the victim’s devices GPS location, Contacts, SMS data, etc., it also collects the PII (personally identifiable information) from the victim mobile without the user knowledge and exfiltrates the data to the spyware hosted Command and Control server.
Default permissions PJobRAT have,
- android.permission.READ_CONTACTS
- android.permission.READ_SMS
- android.permission.RECORD_AUDIO
- android.permission.ACCESS_FINE_LOCATION
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.GET_ACCOUNTS
- android.permission.BIND_ACCESSIBILITY_SERVICE
Another malicious feature that the application collects almost all the information that is available in the device and uploads it to the CnC server,
- Upload address book
- Upload SMS
- Upload audio files
- Upload video file
- Upload image file
- Upload a list of installed apps
- Upload a list of external storage files
- Upload WIFI, geographic location, and other information
- Update phone number
- recording
PJobRAT communication ways
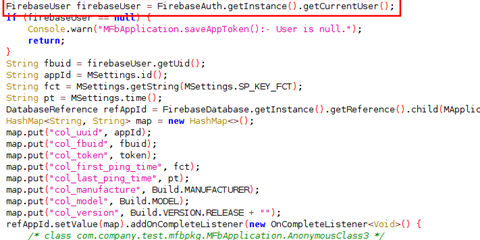
Spyware uses mainly uses 2 communication methods, one is Firebase Cloud Message (FCM) and the other is HTTP which sends the instructions from the server to the client communication through FCM using the message PUSH function.

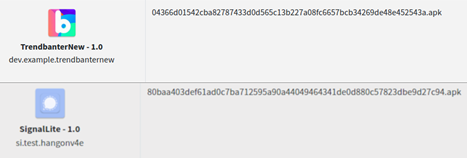
Upon the analysis, the team found that the Trendbanter application is associated with 4 applications and using them upload the victim’s private and critical information. And they are disguised as Instant messaging app Signal and HangOn Messenger and the attack is active since January 2021 according to the security researchers from 360 Firehomes Lab.
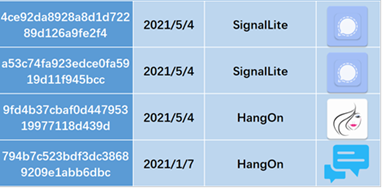
Also based on the similarity of the code structure It is found to have first appeared at the end of 2019 and Trendbanter was speculated as a new version that was developed by the same group of hackers.
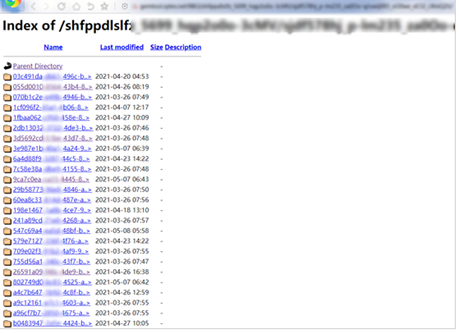
And the stolen data found in the privacy return server where the attackers use to store the information of devices which was compromised, and the server is active and stored more data during 2021. And each folder in the image represents the data uploaded from mobile phones on the attacker’s server.
Indicators of Compromises (IoC)
SHA256
- 5c715ca910ffbd80189cffd2705a5346f40bc466458e0223191d56be5a417c7b
- e8f9b778b87cef1d767a77cb99401875ffdbcc85b345f31a4b4e1b7003218f3f
- 80baa403def61ad0c7ba712595a90a44049464341de0d880c57823dbe9d27c94
- 04366d01542cba82787433d0d565c13b227a08fc6657bcb34269de48e452543a
- 34021375c1720620093699fd98ca2a2856ef4c77f42ff5c8fb02ad194817a235
- 41576737cd3d9f1e04ca0b7d49b412ecc935da78b2ea007c92b84d85012b011e
- c9db17ede3177c6fd13fa90259733dbca9be8fbd43f0059efd6ec35acbda2b48
- f491e27644a85915a1f92314c20e9fc63337a019f9463d34df262699d0a8a7ee
MD5
- 7bef7a2a6ba1b2aceb84ff3adb5db8b3
- 4ce92da8928a8d1d72289d126a9fe2f4
- a53c74fa923edce0fa5919d11f945bcc
- 9fd4b37cbaf0d44795319977118d439d
- 794b7c523bdf3dc38689209e1abb6dbc
- 02998ab92e880db2a1ddbc98f448d828
- 44cd76e590a1c8f0b8a2091884d9f699
- 807668ed4b3bd090a3b5fb57e742be0d
Command and Control
- com.company.test
- com.test.piclock
- com.simple.ppapp
- si.test.hangonv4e
- com.company.hangon
- org.company.hangonv3
- dev.example.trendbanternew
- si.test.hangonv4e
Data upload URL:
- hxxps://helloworld.bounceme.net/axbxcxdx123/test[.]php
- hxxp://gemtool.sytes[.]net:9863/shfppdlslfz_5699_hqp2o0o-3cMV/sjdf578hj_p-lm235_za0Oo-q/sjdf0oO2hq877pnzxii_iioOiupXxw[.]php
- hxxp://gemtool.sytes[.]net:9863/shfppdlslfz_5699_hqp2o0o-3cMV/sjdf578hj_p-lm235_za0Oo-q/sjdf0oO2hq877pnzxii_iioOiupXxw[.]php
- hxxp://gemtool.sytes[.]net:9863/shfppdlslfz_5699_hqp2o0o-3cMV/sjdf578hj_p-lm235_za0Oo-q/sjdf0oO2hq877pnzxii_iioOiupXxw[.]php
- hxxp://gemtool.sytes[.]net:9863/shfppdlslfz_5699_hqp2o0o-3cMV/sjdf578hj_p-lm235_za0Oo-q/sjdf0oO2hq877pnzxii_iioOiupXxw[.]php
- hxxp://gemtool.sytes[.]net:9863/shfppdlslfz_5699_hqp2o0o-3cMV/sjdf578hj_p-lm235_za0Oo-q/sjdf0oO2hq877pnzxii_iioOiupXxw[.]php
- hxxp://144[.]91[.]65[.]101/senewteam2136/mainfiles/file_handler.php
- hxxp://144[.]91[.]65[.]101/senewteam2137/mainfiles/file_handler.php
- hxxps://helloworld[.]bounceme[.]net/axbxcxdx123/test.php
Recommendations:
- Always download and install the trusted applications from reputed websites.
- Keep your software updated with the latest versions.
- Install the antivirus and remove the malicious applications from the device.
- Enable 2 factor authentication and strong passwords.
- It is always important to verify the privileges and permissions requested by application while installing the on the devices.
Reference:
https://www.huxiu.com/article/359760.html
Twitter account: https://twitter.com/blackorbird/status/1404752748919156737?s=20
