As per the security researchers, a new remote access Trojan was detected from Lumen’s Black Lotus Labs which is called as ReverseRat. Upon the analysis, it is confirmed that the threat actor is targeting government and energy organizations in the south and central Asia regions with the infrastructure which is believed to be hosted from Pakistan.
New Trojan was deployed to infect a machine and achieve persistence along with an open-source RAT called Allakore.
ReverseRat uses the evasion technique to avoid the detections as,
- The malware uses the compromised domains of the country as same as the target country entity to host the malicious files.
- After the initial compromise Trojan selects the highly compromised targets.
- The Trojan reuses and modifies the open-source codes for target compromise.
- And it used the In-Memory component during the initial access. Also, to maintain the persistence on the target system the Trojan stealthily modifies the registry files.
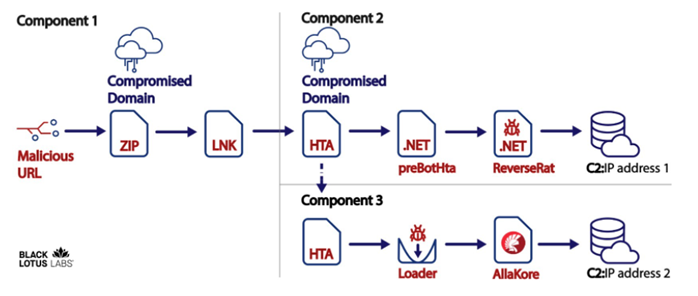
Black Lotus labs upon the investigation confirm that the threat actor is operated from Pakistan. And observed that the Trojan downloads two agents on the infected machine, where one In-memory component and the other resides in the Side-loaded component which grants access to the infected machine to use in persistence mode. But in some instances, researchers believe that bi-directional C2 connections are still ongoing as displayed as component 3 as in the image.
ReverRat Trojan technical analysis
Component 1:
In this phase, the victims were delivered with compromised websites along with the URL redirection. Here the threat actors chose the compromised domains of the country where the targeted company is located to evade detection. While it is not confirmed that how the URLs were delivered to the victims, but likely sent through phishing mail and messages.
The Trojan compromises the victims by when the users click the compromised URLs received will download the .zip file which contains Microsoft shortcut file (.ink) and PDF file. Where the PDF will be executed upon the user interaction and the PDF file creates a decoy to distract the user by executing an HTA file (HTML application) from the compromised website which use to connect the victim.
As per the researchers, the attackers use to lure the users by sending more generic reference containing COVID-19 messages upon which the victim believed it to be genuine and click the same.
Component 2:
Here in the phase the activating the HTA file takes place, where it is retrieved using the JavaScript code from the project called CactusTorch. And the running process is injected with 32-bit shellcode to launch the .NET program called preBotHta.pdb which is active since 2019. This preBotHta.pdb is the placement of ReverseRat Trojan in the infected host. Kaspersky Antivirus has detected the ReverseRat (preBotHta.pdb) will be placed in the MyMusic path, but later it was placed in the Startup folder and it will be displayed in name as tasksmgr.exe. And later iterations of this Trojan were used in the name as Svchostt.exe.
Execution of ReverseRat Trojan
The file preBotHta.pdb starts the execution of ReverseRat by obtaining the information of the following components from WMI services such as,
- MAC address
- Physical memory on the device converted to Mbs
- Information about the processor
- Max clock speed converted to Ghz
- Data width converted to bits
- Name (e.g. Intel® Core™ i7-8569U CPU @ 2.80GHz)
- Manufacturer (e.g. GenuineIntel)
And used the .NET framework to obtain the computer name, Operating system, Public IP address.
ReverseRat Trojan reference the original path for the source code files for the threat actor on the infected machines as on,
c:\Users\Zombie\Desktop\ReverseRat client\ReverseRat\ReverseRat\obj\Release\svchostt.pdb
c:\Users\Neil\Desktop\inform\c\ReverseRat\ReverseRat\obj\Debug\ReverseRat.pdb.
Component 3:
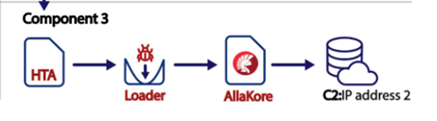
In this component phase, the second HTA file will be retrieved from the compromised domain which initially hosted the. ZIP and first HTA file. Here, the second HTA file contains encoded command to modify the registry key, loader, and the Allakore. And the Allakore remote agent version is revealed once the HTA file is decoded and alternatively provides the details to maintain the access in the compromised network.
Here the threat actor maintains the persistence after rebooting with the target machine’s current user account and modifying the Run registry key to side-load the dropped file by the threat actor.
Command modifying the run registry key:
REG ADD “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /V “WinLogs” /t REG_SZ /F /D “C:\ProgramData\WinLogs\credwiz.exe”.
Along with legitimate windows application credwiz.exe the threat actor side-loader DUser.dll is used for backing up and restoration of the credentials. And AllaKore was terminated once the DUser.dll spawn the CreateProcess functions on the file.
And it is also found that the Trojan files does not come with any encryption methods and it is easily detected by network monitoring tools.
Sample HTTP Communications such as “MAINSOCKET”,
While the researchers says that they have observed similar pattern from the Operation SideCopy campaign, where the first path is the ReverseRat agent internally called Svchostt: C:\Users\be\AppData\Local\Temporary Projects\svchostt\obj\x86\Release\svchostt.pdb,
And the second is the njRAT sample internally called server: C:\Users\be\AppData\Local\Temporary Projects\server\obj\x86\Release\server.pdb njRAT is a well-known and documented agent, it shows that this threat actor like many others may prefer to use publicly available agents over custom builds.
Indicators of Compromise (IoC)
Black Lotus identified few IOCs,
- 175.72[.]105
- 186.189[.]6
- 255.7[.]33
- 188.181[.]224
- 97.142[.]96
- 68.104[.]126
- 86.75[.]119
- 249.40[.]68
- 91.65[.]100
- 68.108[.]22
Additional C2 connections,
- 207.180.230[.]63
- 164.68.108[.]153
- 167.86.97[.]221
- certindia.ignorelist[.]com
- defencecyberorg.myddns[.]me
- certindia.chickenkiller[.]com
- coronavirusupdate.ddnsking[.]com
For additional IOCs associated with this campaign, check this page: https://github.com/blacklotuslabs/IOCs/blob/main/Reverserat_iocs.csv
Conclusion:
This threat actor should be monitored continuously, as threat actor doesn’t seem to be having influence as the most state-skilled sponsored actors. While it targets the South and Central Asian regions as they proven to have gained a network access. It will be real threat to the organizations beyond the regions specified. So organizations need to vigilant on these threat actor presence and take necessary action before the anything is compromised.
