Cybersecurity Incident Response is a process of the Organization to detect, prevent and eradicate malicious incidents, threats, attacks that breach the company networks. . This is important for a security analyst to know what the next steps are once there is an incident occurred.
The incident response life cycle is a framework that is used in handling cyberattacks. The Incident Response cycle contains six steps of response cycle which contains Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned.
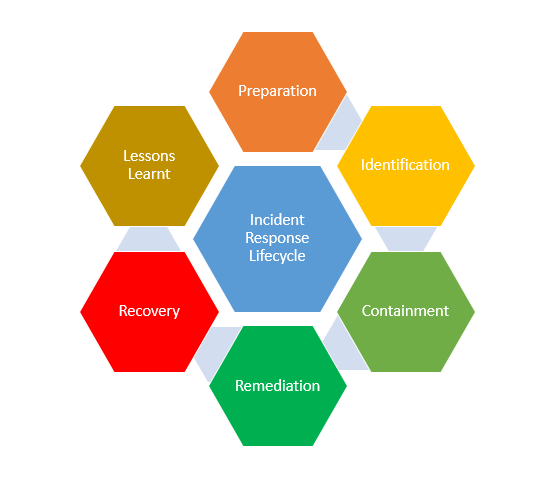
Overview of Incident Response cycle
1. Preparation
Incident Response initial step is preparation for the incident response so the organization is ready to respond and react to the incidents and also ensures by preventing all the data and assets of the corresponding organizations.
Queries to address in the Preparation step:
- Does the Incident Response team know about the alerts and use cases that been notified for further analysis?
- Does the security Analyst been trained on the security policies of the company?
- Is the Incident Response plan been tested and approved by the company?
- Is the Security analysts been given proper training and awareness on the latest technology updates?
2. Identification
This is the second phase of the incident response cycle, it is the crucial step where it is important to identify if the systems have been compromised or not. This is very critical to detect the origins of the incidents and threats. Also should be able to check if all the systems have been compromised from the enterprise malware attacks.
Security Analysts from SOC Operations should be able to trace the adversaries like Techniques, Tactics of the incident and deploy a proper countermeasure before any data exfiltration happens. This is also the first step towards the proper remediation of the incidents.
MITRE attack websites give more in-depth information on the latest threat groups Tactics, Techniques, and mitigations for both Enterprise and Mobile platforms.
Queries to address in Identification:
- Where the incidents did were Originated from?
- What are all the critical ports that were accessed during the possible breach?
- Where the reputations of port numbers and IP address been verified to ensure if it’s a clean or part malicious campaign? – Virus Total, Hybrid Analysis, IBM intelligence Few Platforms to check and validate the IOCs reported in the incidents.
- What is the scope of the assets that were impacted?
3. Containment
While analysing the incidents we will understand how the initial breach has occurred and, what is the impact based on this information it would sometimes require to contain the system or infected server from the network so that it would not spread the infection within the connected network.
During this stage, Threat-Intelligence will be handy for a security analyst to identify the infection traits and act upon them accordingly.
Few queries to address in this state:
- What is the scope of devices and Networks that is been infected?
- What level of containment done in the network, Assets, User to stop the infection?
- Is the backup is taken in the case production environment?
- Is all the compliance checks been completed in all the contained an infected system?
- Does user remote access is enabled with MFA (Multi-Factor Authentication).
4. Eradication (Remediation)
After containing the infected system, its recommendation to take immediate action on the details collected during the analysis. Below are the few points to ensure actions on the incident right away,
- Blocking the unknown IP, Malicious IP address.
- Blackhole the malicious domain names from the environment.
- Verify the remediation activities like patching, re-imaging the infected system and resetting the user credentials, etc.,
5. Recovery
Recovery is the process of starting or moving the business back to normal day-to-day activities. However, in the long-term is important to implement security measures on the network to prevent similar cyber-attacks in the feature incidents.
Few options include in this stage:
- Network re-design is required if the network is breached.
- Enforcing the proper Change Management process program.
- Authentication Model to be improved at the enterprise level.
- Checking the Centralized logging system and establishing the security awareness programs.
6. Lessons Learned
Once after completing the investigation it’s important to check if all the mitigation steps have been completed and additional countermeasures are being implemented. This is where we should be having meetings with the stakeholders of the enterprise and discuss the lessons learned from the latest incident or attack. And documenting the entire investigation and everything about the incidents to prevent the feature attacks.
Things to follow in this stage:
- To ensure a similar breach doesn’t happen again.
- What was the exact exploit in the recent breach?
- What improvements to be taken to protect the Organizations security measures?
Conclusion :
The complete Incident Response lifecycle that every Enterprise follows during the Incident alerts with improved security policies along with Security Operation (SOC) management to keep the Organization safe and secure from cyber-attacks. It is also crucial to keep updated on all the latest threats and attack techniques used by Cyber Criminals.
