Pyramid of pain is an interesting and important topic of Cyber threat Intelligence and Threat Hunting. It was first introduced in 2013 by Security professional David J Bianco Its main focus on incident response and threat hunting methodologies which gives the purpose for you to detect an adversary of the attack vectors.
As attack Indicators contains Hash, IP address, Domain Names, Network, Host Artifacts, Tools, TTP which comprises of Pyramid structure as below,

- Hash Values (Trivial) – As per Microsoft, hash values are considered as “numeric values of a fixed length that uniquely identifies the data”. And this is used as a signature in the attack detections (SHA1, MD5, and SHA256). We might have seen the hash value of the data during the developer creates and uploads it, as this confirms the authenticity of the downloaded file.

In the figure, you can see that Kali Linux files are given with Hash values as they should not be tampered with by the hackers and maintain the file genuinely provided by the vendor.
Another sample from putty download file with the signature of hash values.
2. IP Address (EASY) – The IP Address as an adversary is used as an identifier that can be hidden with the anonymity to the proxy, VPN, Tor for example. In case if the IP address is hardcoded then it can be blacklisted and prevented for further communication, also it might for some security controls to detect if the IP address is hardcoded or Spoofed with genuine IP.

Artifact sample for Malicious IP address as an IOC
3. Domain Name (SIMPLE) – Domain Names are not the numeric values as IP address, they contain actual domain names (google.com) or subdomain domains within the domains (google.image.com), etc., Domain name artifacts can be found in Proxy logs for the artifact analysis for DNS analysis like DNS attacks.
One of the DNS attacks is redirecting the traffic to the malicious domain name which looks genuine to the victim as below, for example, Punycode is special in converting the Unicode characters into ASCII values that are used Hostnames.
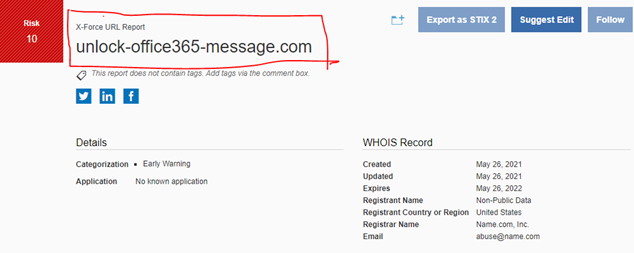
Here, office 365-message.com is malicious is because doesn’t have a proper domain name ending
4. Network/Host artifacts (Annoying) – These are all the clues for an adversary to check for the network packets and also which annoying for the attackers to clear the paths in endpoint systems. Host artifacts might contain Registry values, Unwanted Process execution, and Spam application running in the endpoint, etc., whereas Network artifacts contain the browser agent which is rarely or not used for official purposes like Tor Browser, unwanted traffic on non-traditional ports, ie, Port number: 50001.
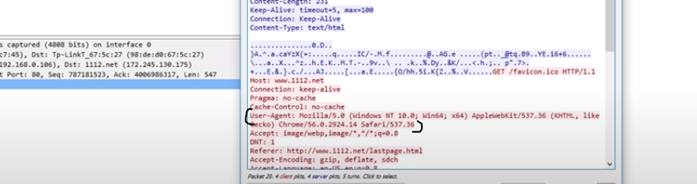
Example of Wireshark event capture for network artifact to show user agents used (Mozilla, chrome, IE, etc.)
5. Tools (Challenging) – Most of the time attackers and incident responders use tools to attack and detect the adversary of the threats. Some of the tools might help the attackers to create the exploit of the victim, scan the victim network for targeted attacks, IR analysts will have to use the tools like SIEM, IDS, and EDR to detect/hunt the insider malware threats within the networks which are most challenging. For Example, APT groups will most of the time stick to the set of tools they use during penetrating the target network.
6. TTP (Tough) – TTP represents the signature methods of the attacker or group of hackers like APT. Here tactics refer to attacks behaviour, technique refers to the one which uses one of the tactics which the attacker used to Proceed with proper Procedure techniques to attack the target victims. In this case, it’s a tough and time-consuming process for the attackers to implement this type of attack using TTP. For more details, you can visit the MITRE Att&ck Website.
