The Cyber kill chain is the term which was initially started from the military, the military term as kill chain. Here cyber kill chain model has different stages of an attack cycle by which it identifies the adversaries that attackers try to achieve their objectives.
In the cyber kill chain model, every intrusion is a chance to understand more about the adversaries and use their persistence to our advantage of Organization requirements. Kill chain model is designed by 7 stages of Cyber-attack, we will see in detail further,
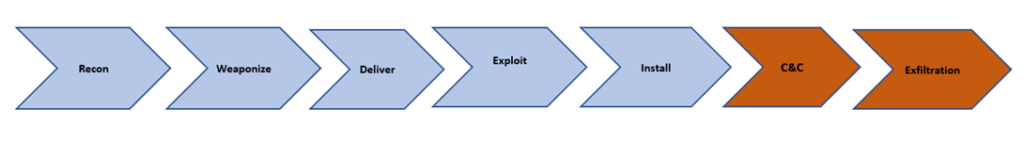
Cyber Kill Chain Model
In the Cyber Kill Chain model, first 5 stages area known as Intrusion stage and whereas the last 2 stages are known as active breach stage.
1. Recon
In this step, it involves passive scanning with OSINT (freely available Internet data). And also involves active public IP scanning, Domain Names search, etc.,
Adversary for Recon: It includes the adversaries which would help the attackers achieve their objectives.
- Email address harvesting.
- Tracing employees on social media networks.
- Discovery of Internet-facing servers list.
Recon Detection: Detecting recon initially will be very difficult as it happens, but with the proper defenders in place, it would be easy to track the intent of the adversaries.
- Log collection of the website visitor for alerting and historical searching.
- Try to build detections for browsing behaviour that is unique to the recon phase.
- Web administrators to collaborate and utilize the existing browsers analytics.
- Giving more priority to defender technologies based on recon activity.
2. Weaponize
In this stage where the RAT (Remote Access Tools) is added to the exploit. The exploit can be embedded with malicious documents via email attachments called phishing techniques. And this stage also involves the method of delivering the exploit.
Adversary for Weaponization – Here the adversaries are in the preparation and staging phase of their operation. Malware uses automated tools and exploits into a delivered payload.
- For file-based exploits, select the “decoy” document to deliver to the victims.
- Embed/Compile the backdoors and weaponize the payload.
- Implement the appropriate CnC infrastructure operations.
- Designate a specific “Campaign Name” and embedded in the malware.
Weaponize detection: Defenders might not detect the weaponization phase as it happens. It can be detected only through the malware artifacts which are most durable and can withstand the standard defender tools.
- Always conduct the complete malware analysis like how the payload was created and dropped in a victim machine.
- It is always recommended to build a campaign name to identify the weaponized toolkit, so attackers do not reuse them in different scenarios.
- Collect artifacts and metadata for future analysis of available IOCs of the malware used in this phase.
- Verify the specified APT group involved in the recent malware campaigns and determine the common artifacts.
3. Delivery
In this phase, the weaponized tool is delivered to the victim for further exploitation and installation. Delivery could be through phishing mail or social media data transfer and any other mode of malware transfer to the targeted victims.
Adversary for Delivery – In this phase, it conveys that the malware is delivered to the specified targets.
- Directly delivering the malware to web servers in a controlled manner.
- Releasing the malware through a different form such as,
- Phishing email attached with malware embedded pdf, Documents, Excel, etc.,
- Malware from an infected USB stick.
- Sharing malicious files through social media.
- “Watering hole technique” for compromised websites.
Deliver phase detection: This will be the first and most critical opportunity for defenders to block the operations by detecting the malware in the victim’s machine by the defenders /Antivirus.
- First understand the targeted devices, people, and their roles and responsibilities with the information available.
- Leveraging the weaponized artifacts will help in detecting the new malicious payloads at the time of malware delivery.
- Analyzing the dwell time of the malware delivery.
- Using Forensic analysis will help us determine the artifacts that were collected from email and weblogs to understand how the delivery has happened in the initial stage.
4. Exploit
This is the exploitation phase of malware where the user downloads the attached malicious documents or clicks the malicious URLs from the phishing emails received. Here, the malware uses 2 step process where it first downloads the actual RAT (Remote Access Tools) and executes the malware in the memory storage where it does not consume much system resource for the exploits to perform.
Adversary for Exploit – here, exploiting a vulnerability to gain access of the target. Mostly Zero-day technique refers to the exploit codes used.
- Detecting the vulnerabilities from the software or hardware.
- Developing or Acquire the Zero-day exploit.
- Victims triggered exploits such as Opening attachments of malicious emails or clicking the malicious link from the phishing email.
- Analyse the exploits triggered for server-based infrastructure.
Exploit detection: Detection of the Zero-day vulnerabilities will be necessary to stop the exploits at this stage.
- First to have user awareness training and email testing, employees.
- Develop secure coding training for web developers.
- Implementing regular vulnerability scanning and penetration testing will keep the policy and process secured and updated.
- Using Forensic techniques to audit the origins of the malware exploits.
- Endpoint security measures like restricting the user admin privileges, custom rules to block the shellcode execution, etc.,
5. Install
Installing the malware tools via RAT which was delivered initially. Other techniques can be installing the Keylogger, Network scanner, etc.,
Adversary for install – Installs the persistent backdoor or implant in the victim environment to maintain access for a long time and execute the malware when required.
- Installing the web shell on the target web server.
- Implant or install the backdoor on victim machines.
- Creating point for persistence by adding Autoruns Keys, Registry changes, Services, etc.,
Install Phase-detection: In this phase, the endpoints to detect and log the installation activities.
- Understand whether the malware requires admin privileges or only user access to install malware.
- HIPS to alert / Block on common installation paths such as recycler, Temp folders, etc.,
- Detect abnormal file creations.
- Certificate extracts of signed executables.
6. C&C
This is Command and Control phase, in this stage the victim’s machine will communicate with the IP address or domain and provide the adversary command-line access to the attacker system.
Adversary for C&C – Here, the malware opens the C&C channel to the attackers to manipulate the exploits in the victim system.
- 2-way communications channel to C2 infrastructure.
- Common C2 channels are over email protocols, Web, and DNS.
- C2 channels might be controlled by an attacker or Victim system which is infected botnets.
C&C detection: Defender’s last best chance to block the operations controlled by C2 infra. By blocking the communications adversaries will lose the connections further.
- Discover C2 infrastructure with thorough malware analysis.
- Block the C2 protocols on web proxies traffic networks.
- Customize the proxy category to block the “none” or “uncategorized” domains.
- DNS sink holing techniques and DNS server poisoning monitoring.
7. Action on Objects / Exfiltration
This is the final stage where the goal is achieved. And this happens when the adversary scans the network, looks/reviews data, and grabs what information they are looking for in the victim machine. And what data is leaving the network when it’s protected.
Adversary for Exfiltration: Achieve the mission’s goal by the intruders by extracting the data from the breached networks.
- Collect user credentials.
- Privilege escalations.
- Internal reconnaissance.
- Lateral movement within the infected network.
- Collect and exfiltrate data.
- Destroy systems, Overwrite or corrupt data.
Exfiltration detection: The defender should be able to detect the data exfiltration as quickly as possible.
- Creating the Incident response playbook and communications plans.
- Detect data exfiltration, lateral movement, unauthorized access & credential usage.
- Network package capture to recreate activity.
- Conduct damage assessment with Subject matter experts.
Conclusion:
Analysis of the multiple intrusion kill chains over time draws attention to similarities and overlapping indicators. And defenders will learn to recognize and define intrusion campaigns and understand the intruder’s objectives.
Identifying the patterns like what they are looking for, why are they targeting?
Understanding the patterns or techniques used by the attacker will help in identifying how best to protect from the next cyber-attacks. And the goal of the defender is to stop the adversaries from progressing up with the kill chain and stopping them. Analysing them in the early stages of the chain is always preferred and for this to understand the need to learn about the Cyber Kill Chain model as stated above.
